A Deep-Dive Analysis for CISOs on the Next Generation of Browser Credential Theft
A new Windows-based information stealer named Sryxen is gaining traction in underground markets as part of a fast-evolving Malware-as-a-Service (MaaS) ecosystem. Unlike earlier generations of credential harvesters that required breaking Chrome encryption or manually extracting browser databases, Sryxen bypasses Google Chrome’s App-Bound Encryption altogether, by using Chrome itself as a decryptor.
This technique marks a critical shift in the evolution of stealers: attackers no longer try to defeat cryptographic protections. They simply force the protected application to decrypt its own data and hand it over.
This article explains how this attack works, why it matters for enterprise risk, and what CISOs must consider to defend against this rapidly emerging threat.


A New Paradigm: Abusing Chrome Instead of Breaking It
Google introduced App-Bound Encryption in Chrome version 127+, binding sensitive information—such as cookies and authentication tokens—to device-specific keys stored through DPAPI. This significantly limited traditional stealer techniques that grabbed encrypted SQLite files and attempted local decryption.
Sryxen moves in a completely different direction.
Rather than attacking the encryption, it attacks the application trust model.
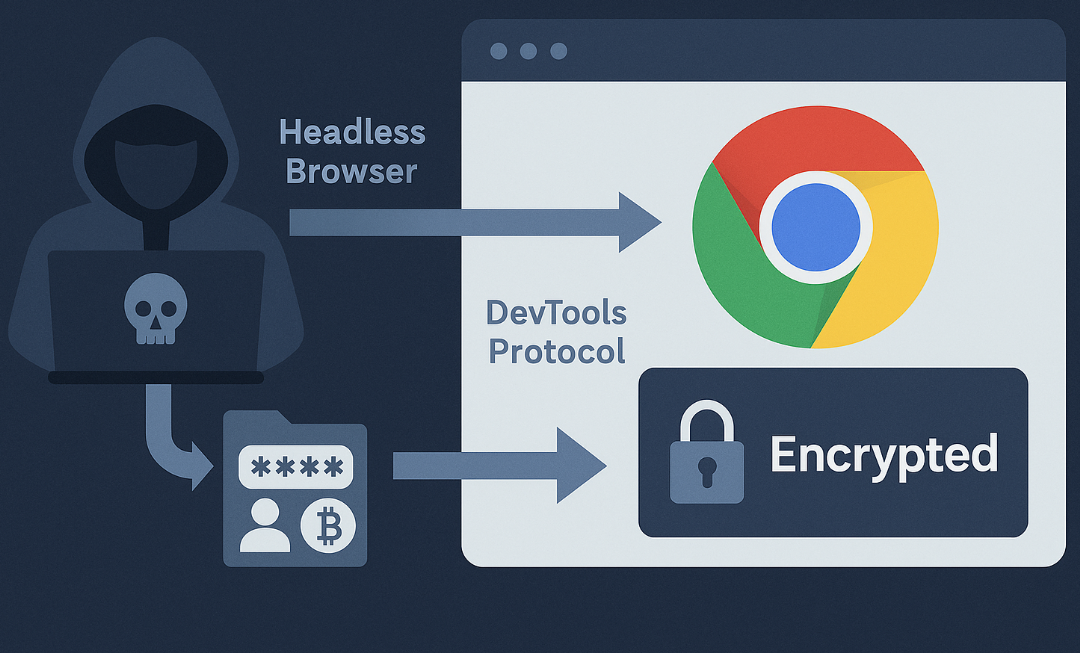
The malware launches Chrome in headless mode with developer debugging capabilities enabled, and then issues commands through Chrome’s DevTools Protocol to request all cookies, fully decrypted, via:
Network.getAllCookies
Chrome processes the request internally with its own decryption keys, then returns plaintext cookies directly to the malware. The decrypted data never touches the disk—eliminating opportunities for file-based detection.
This is not an exploit. It is a legitimate Chrome feature turned against the user.
How Sryxen Works: Technical Breakdown
Sryxen is written in C++ and optimized for ultra-fast, non-persistent execution. It runs once, steals everything it can, and exits. No persistence, no registry modifications, minimal artifacts.
Anti-Analysis & Evasion Layers
Researchers have identified several defensive layers built into Sryxen:
- Vectored Exception Handling (VEH) encryption: keeps the payload encrypted at rest and decrypts it only through exception triggers, making static analysis nearly impossible.
-
Six anti-debugging techniques, including:
- PEB structure inspection
- NtGlobalFlag checks
- Hardware breakpoint detection
- Debugger presence API calls
If any debugging environment is detected, the malware terminates instantly.
These defenses reflect trends seen in modern families such as Vidar, Lumma, Atomic, and Raccoon v2—but Sryxen’s implementation is notably more aggressive.
Bypassing Chrome App-Bound Encryption
Once Sryxen detects Chrome version 127+, it switches into “bypass mode.”
- Terminates existing Chrome processes to avoid database locks.
-
Relaunches Chrome headless using flags such as:
--headless --remote-debugging-port=9222 --user-data-dir=C:\Users\<victim>\AppData\Local\Temp\<random>\ - Establishes a WebSocket connection to Chrome’s DevTools Protocol.
-
Requests decrypted cookies using:
Network.getAllCookies -
Harvests additional browser data, including:
- passwords
- session tokens
- autofill contents
- cryptocurrency wallets
- Exfiltrates data via a Telegram bot using curl + PowerShell.
This creates a complete, high-value data package suitable for immediate account takeover and further monetization.
Where Sryxen Fits in the Stealer Ecosystem
Recent years have seen a surge in sophisticated stealers:
- Glove Stealer (2024) first demonstrated App-Bound Encryption bypass through browser automation.
- Vidar (2025) implemented direct memory injection to extract credentials.
- Lumma Stealer (2024–2025) leveraged browser fingerprinting and CDP communications.
Sryxen combines elements of these approaches but is distinguished by:
- Complete reliance on native DevTools Protocol
- Full headless browser control
- Aggressive anti-analysis stack
- No persistence and very small forensic footprint
This makes it one of the stealthiest approaches to cookie extraction currently observed.