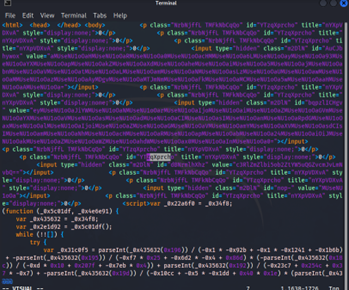
Phishing attacks continue evolving, with Blob URI phishing emerging as a sophisticated, stealthy method that bypasses traditional security checks. By exploiting browser-native features like Blob and URL.createObjectURL, attackers create fully in-memory fake login pages that never touch the network or disk. This makes detection by antivirus or firewalls extremely challenging.
A typical attack involves injecting malicious JavaScript into a trusted page, generating a Blob URI that looks like it belongs to the legitimate domain, and opening a fake login page. Users see familiar URLs without suspicious indicators like wrong certificates or unexpected domains. Attackers often add obfuscation and encryption to hide their code and delay detection.
Defending against Blob URI phishing requires layered strategies: enforcing strict Content Security Policies that block blob: URLs in scripts, monitoring unusual browser behaviors via endpoint detection tools, restricting untrusted browser extensions, and educating users to verify URLs carefully and use password managers.
As this technique grows in use among advanced attackers, organizations must adapt quickly to this new, elusive phishing threat.
Whitepaper