The Lockheed Martin’s kill chain model as a threat assessment and prevention tool is no longer adaptable to the new cybersecurity world because there are too many attack vectors.
In addition, this methodology reinforces traditional defensive strategies based on perimeter and malware prevention. This is particularly problematic given the likelihood of successful attacks that breach the perimeter of the internal network .
In 2017 Paul Pols in collaboration with Fox-IT and Leiden University described in a very detailed whitepaper a new framework for overcoming common criticisms against the traditional cyber kill chain, combining Lockheed Martin’s kill chain and MITRE’s ATT&CK ® framework. The unified version of the kill chain is an arrangement of 18 unique attack steps that can occur in a cyberattack covering activities that occur outside and inside the defended network.
The framework created by Paul Pols is very interesting, however I would like to point out that it does not yet reflect the attacks that are found in today’s world.
Working for many years as a CISO I realized that attack vectors are not sequential anymore, but they almost all arrive in parallel. From my point of view, cyberattacks are unfortunately very successful because models fail to represent attacks in the most accurate way. The execution time between the first trial and the final destruction has shortened considerably.
It’s like playing a game of chess. Each player can move one figure at a time, however the figures attack or defend the various zones of the chessboard simultaneously.
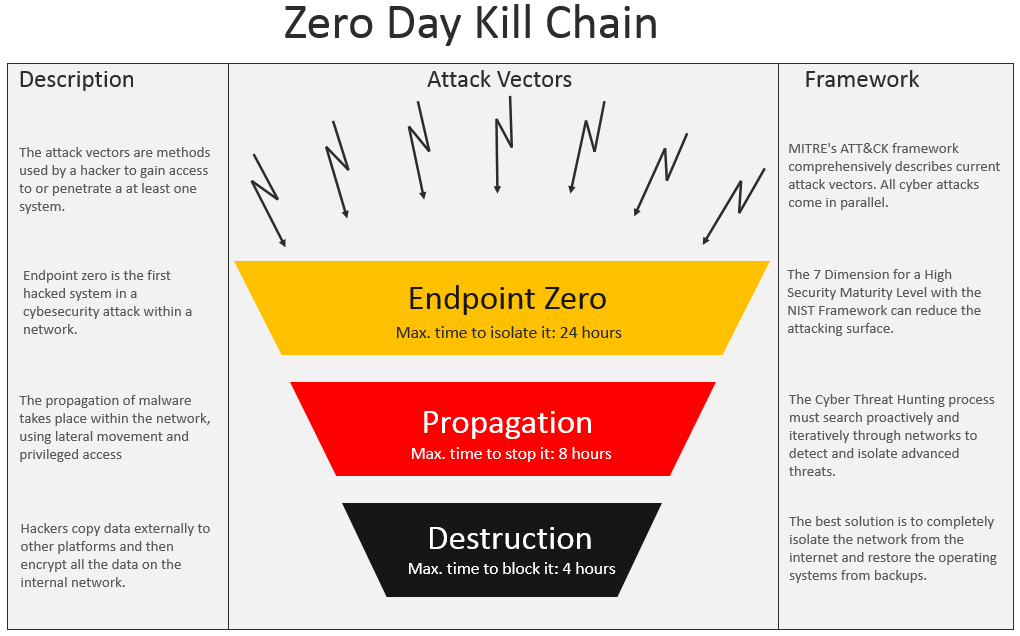
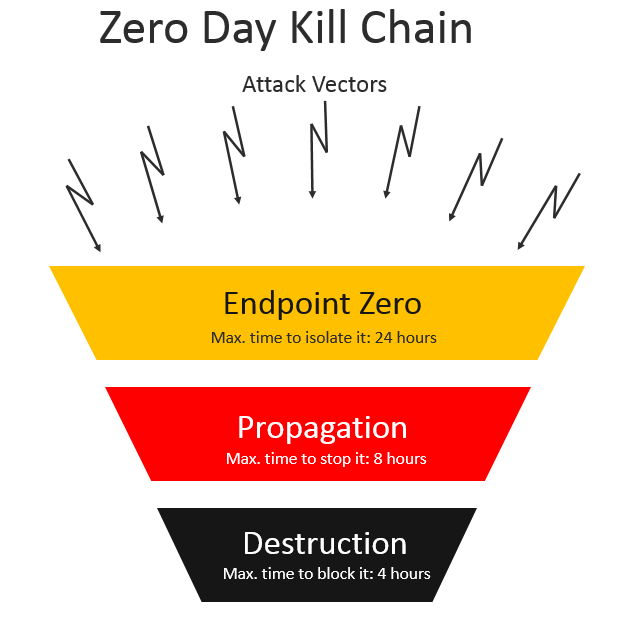
Hackers try via all available vectors to infect at least one endpoint. In cybersecurity, an attack vector is a method used by a hacker to gain access to or penetrate a system.
As in the field of medicine I have defined it as: Endpoint Zero.
Modern cyberattacks use multiple vectors that propagate nearly all in parallel with automated tools and strategies. Cyberattacks can be internally or externally generated and they usually attack the weakest element in a chain. It’s a persistent brute force attack.
For these reasons I propose a new model called “Zero Day Kill Chain” based on tree rapid phases, where all attacks occur in parallel and where the maximal time to find the right step is considerably short.
The phases are:
• Phase 1: Endpoint Zero
• Phase 2: Propagation
• Phase 3: Destruction
In the next image you find the graphical representation of the proposed model.