Introduction
Scalable Vector Graphics (SVG) are widely used because they are crisp at any resolution, small in size, and easily styled or animated. However, this flexibility introduces a serious security concern: SVG files can embed JavaScript that executes automatically without user interaction—so-called zero-click execution.
Recent questions and research show that the threat goes beyond inline scripts. SVGs can:
- Reference external JavaScript files.
- Encode or obfuscate malicious code to evade detection.
- Combine on-screen messages with automatic redirection.
-
Trigger code execution without
onload, simply by including<script>blocks.
How Zero-Click Execution Works
Unlike JPEG or PNG images, an SVG is XML-based and becomes part of the DOM when loaded inline or opened directly. This means:
-
<script>elements can run immediately. -
Event attributes like
onloadoronmouseovercan call JavaScript. - Encoded payloads can be decoded and executed at runtime.
- External script files can be pulled in and executed in some contexts.
Minimal Example
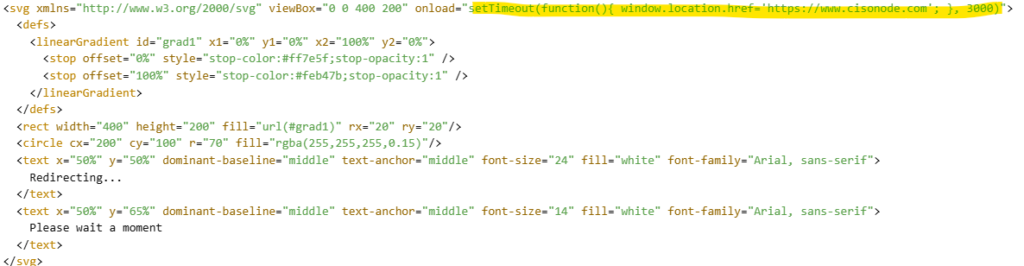
Encoding and Obfuscation
Attackers often encode JavaScript to hide it from simple scans.
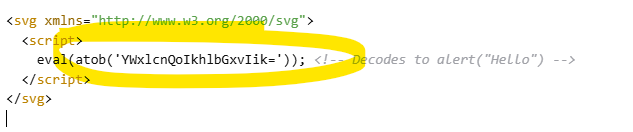
Why This Is Dangerous
- No Click Needed – Runs automatically when parsed.
- Bypasses Click-Based Defenses – No phishing click required.
- Obfuscation – Hides payload from simple scanners.
- External References – Allows dynamic loading of malicious code.
- Misplaced Trust – Many systems treat SVGs as “safe” images.
Mitigation Strategies
- Sanitize all SVGs – Remove scripts, event handlers, and unsafe attributes.
-
Serve as static files – Use
Content-Disposition: attachmentto force download. -
Avoid inline embedding – Prefer
<img>tags (though still sanitize). -
Enforce strong CSP – Restrict script sources and disallow
data:URLs if possible. - Validate upload sources – Accept SVGs only from trusted origins.
Conclusion
SVGs are not just images—they are active documents capable of executing code. They can embed JavaScript directly, load it from external sources, and hide it through encoding or obfuscation. In the wrong hands, this capability enables zero-click attacks that can steal data, redirect users, or compromise systems without any interaction.
Treat SVGs like HTML: sanitize, restrict, and monitor. Never assume that just because a file is “an image,” it’s harmless.
