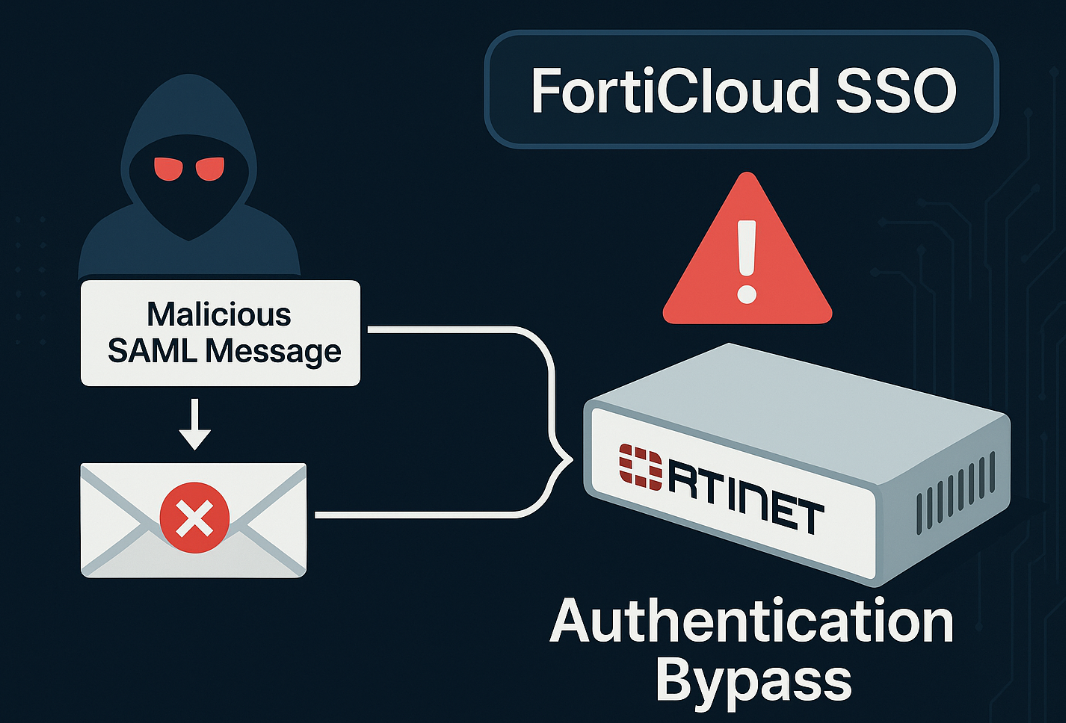
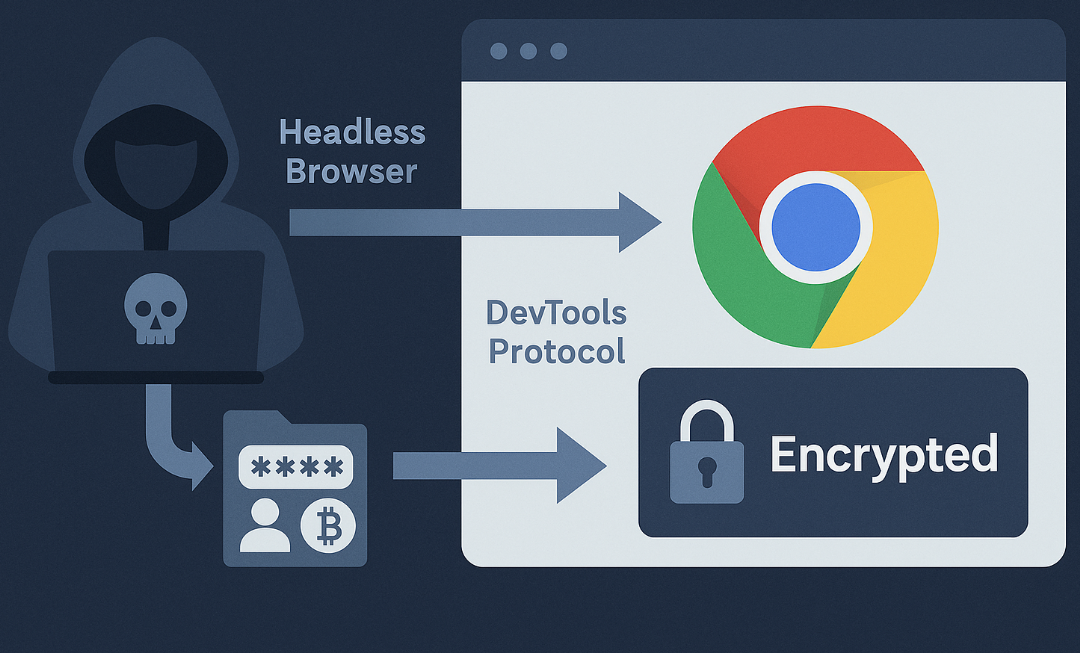
Data Centers, AI Growth and Clean Energy: Why CISOs Must Care About the New “Power-First” Infrastructure Model
As AI accelerates, power becomes a security issue. New “power-first” data center models co-locate clean energy and compute, reshaping resilience,…