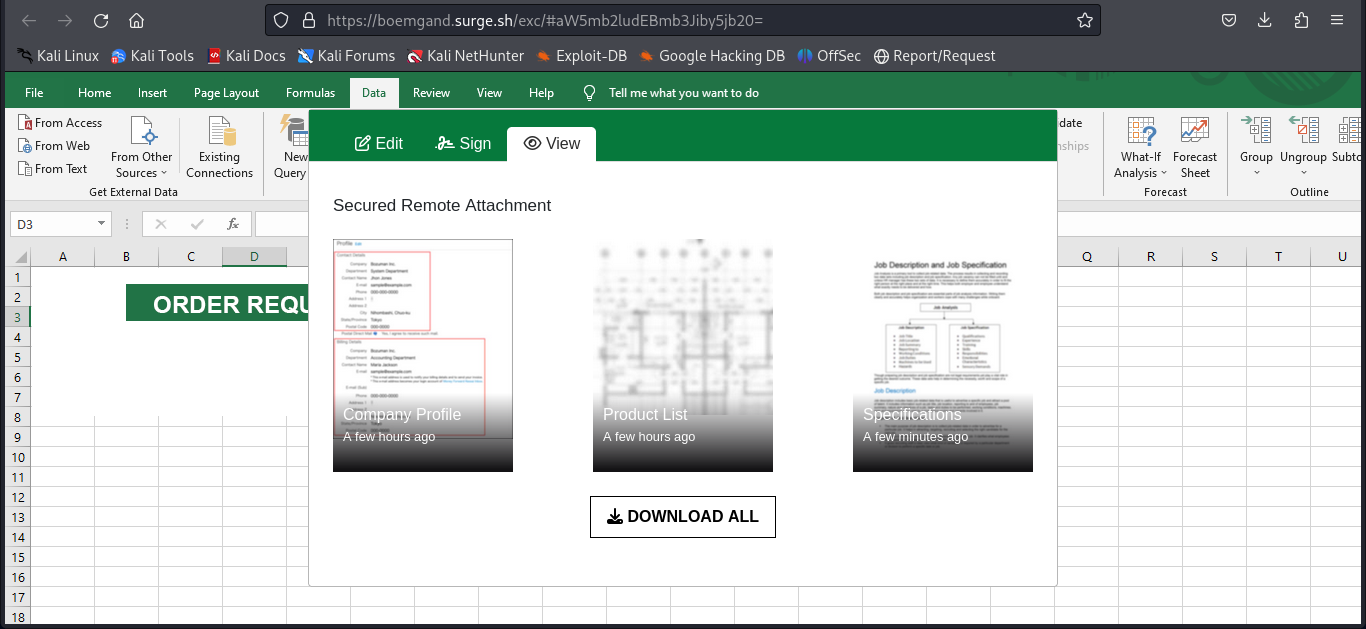
Summary:
Cybercriminals are deploying increasingly deceptive phishing techniques designed to bypass traditional user awareness and security filters. A recent campaign uncovered by our cybersecurity team demonstrates a new method where attackers simulate a familiar Excel file-sharing environment to trick users into entering corporate credentials.
The Attack Vector: Familiar UX with Malicious Intent
In the observed case, the phishing page closely resembles a legitimate Excel document containing a list of shared files. Prominently displayed is a “Download ALL” button, encouraging the user to act quickly — a classic example of urgency-based manipulation. When clicked, the button redirects users to a login form requesting their username and password.
The psychological manipulation is clear: users believe they’re accessing internal shared documents. The realistic interface bypasses common suspicion and makes this phishing attempt especially dangerous in enterprise environments where Excel-based collaboration is standard.
Social Engineering + Technical Camouflage
This campaign employs a multi-domain infrastructure:
-
Initial hosting domain:
boeamand.surge.sh -
Credential collection endpoint:
mon.lifelearner.cloud(IP:209.74.74.23)
Through traffic analysis (including TCP dump evidence), we identified that while the frontend resides on a static site provider (surge.sh), the credentials are exfiltrated via the mon.lifelearner.cloud subdomain — likely registered via Namecheap.
This separation of UI and backend exfiltration is a tactic to evade blacklisting and detection by legacy anti-phishing solutions that may only scan the top-level page.
Why This Matters
- Traditional email security tools may not detect this vector, as links often redirect through benign platforms.
- Credential harvesting is done via HTTPS, making deep packet inspection ineffective unless SSL interception is in place.
- Users are not downloading any files, so there are no malicious attachments to scan — just form fields inside a styled webpage.
Actionable Indicators of Compromise (IOCs)
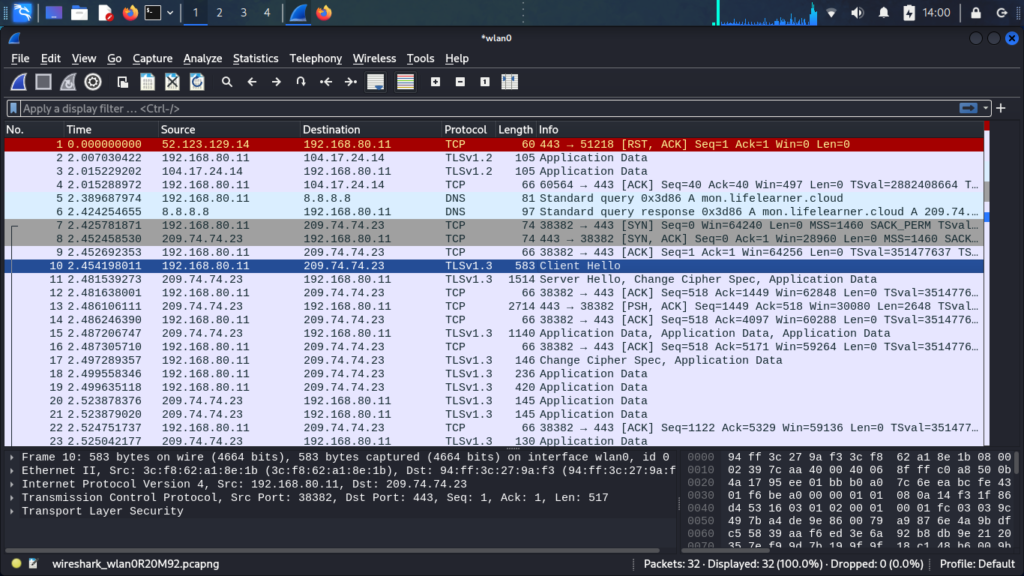
Defensive Recommendations
- Domain Monitoring: Monitor DNS logs for suspicious domains
- Educate Users: Raise awareness about phishing attempts using “document preview” or “download” baits.
- Web Proxy Policy: Block domains with short TTLs or unusual TLDs (e.g.,
.cloud,.sh), particularly when not in use by your organization. - Browser Isolation: Implement browser isolation technology to contain credential entry to trusted domains only.
- Credential Reuse Audits: Enforce MFA and monitor for password reuse after such incidents.
Final Thoughts
This phishing technique showcases the evolution of threat actor sophistication — blending convincing design, multi-domain deception, and cloud infrastructure abuse. As defenders, we must anticipate these developments, integrate behavioral analytics, and promote contextual awareness training.
Let this be a reminder: the weakest link is no longer just a careless click — it’s a familiar interface used against us.