The Problem with CTR: A Negative Legacy
For nearly two decades, Click-Through Rate (CTR) has been the standard metric for measuring user awareness in phishing simulations.
It counts how many employees click on a malicious link — a negative metric that treats mistakes as failures rather than learning opportunities.
But in modern organizations, CTR no longer tells the real story.
Email gateways, sandboxes, and automated filters often “click” links during inspection, generating false positives.
Meanwhile, employees face pressure and fatigue, turning awareness programs into stress tests rather than meaningful education.
In short, CTR is outdated — it measures human fallibility, not systemic resilience.
A Positive Paradigm: Measuring Success, Not Failure
In the AI era, resilience must be measured not by who clicked, but by how fast threats are neutralized.
Cybersecurity has evolved from a human-only discipline into a symbiosis between AI and people.
Every time a phishing email is automatically quarantined, a suspicious URL is isolated, or a vigilant user reports an attack before clicking — that’s a success.
These signals together form a positive resilience model: an indicator of strength, not weakness.
This idea gave birth to a new quantitative metric — the Automated Resilience Index (ARI).
Introducing the Automated Resilience Index (ARI)
The Automated Resilience Index (ARI) measures how fast and how autonomously an organization neutralizes phishing threats.
It’s not about blame or behavior — it’s about system efficiency and speed.
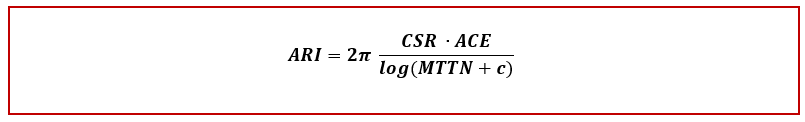
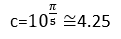
Where:
| Variable | Meaning |
|---|---|
| CSR | Containment Success Rate — % of threats neutralized before reaching users |
| ACE | Autonomous Containment Efficiency — % of mitigation handled automatically by AI/SOAR |
| MTTN | Mean Time To Neutralization (seconds) — average time between detection and elimination |
| 2π | Calibration constant ensuring interpretability (~10-point scale) |
| c=4.25 | A normalization factor that ensures the ARI function remains stable and bounded, preventing division by zero and aligning the resilience curve with typical MTTN distributions observed in operational environments |
The result is capped between 0 and 10, where 10 represents instant, fully automated containment.
Why ARI Matters
Traditional phishing awareness programs penalize clicks.
ARI instead rewards speed and automation — how well the system reacts before users get involved.
- Positive psychology: encourages improvement rather than blame.
- Data-driven: based on measurable, real-time parameters.
- Automation-aligned: integrates with modern SOC and SOAR workflows.
- Predictive: correlates directly with exposure windows — the time before users might click.
According to studies by Microsoft, Verizon, and Google TAG, over 10–15% of users click within the first minute of receiving a phishing email, and half click within five minutes.
Therefore, neutralizing a threat within 60 seconds means blocking the majority of possible incidents — before they even start.
Example Scenarios
| Environment | CSR | ACE | MTTN (s) | ARI |
|---|---|---|---|---|
| Fully automated SOC | 1.0 | 1.0 | 0 | 10 |
| Semi-automated response | 0.9 | 0.9 | 10 | 4.41 |
| Manual intervention | 0.8 | 0.6 | 60 | 1.67 |
Even small gains in automation can dramatically increase resilience.
A reduction from 60 seconds to 10 seconds multiplies ARI several times — showing how speed directly translates into security.
Beyond Awareness: The AI-Human Alliance
Phishing is no longer just a human problem — it’s a systemic response problem. An organization’s success depends on how seamlessly AI, automation, and humans collaborate.
ARI quantifies that collaboration.
It moves cybersecurity measurement from negative detection (“Who failed?”) to positive orchestration (“How effectively did our ecosystem respond?”).
About the Author
Gianclaudio Moresi is the CISO of Forbo Group AG and founder of the Cyber Risk Evaluator (CRE) platform, which quantifies cybersecurity posture through AI-based assessment models.
He also co-organizes the Swiss Cyber AI Conference in Lugano, an event dedicated to the convergence of artificial intelligence and cybersecurity.

