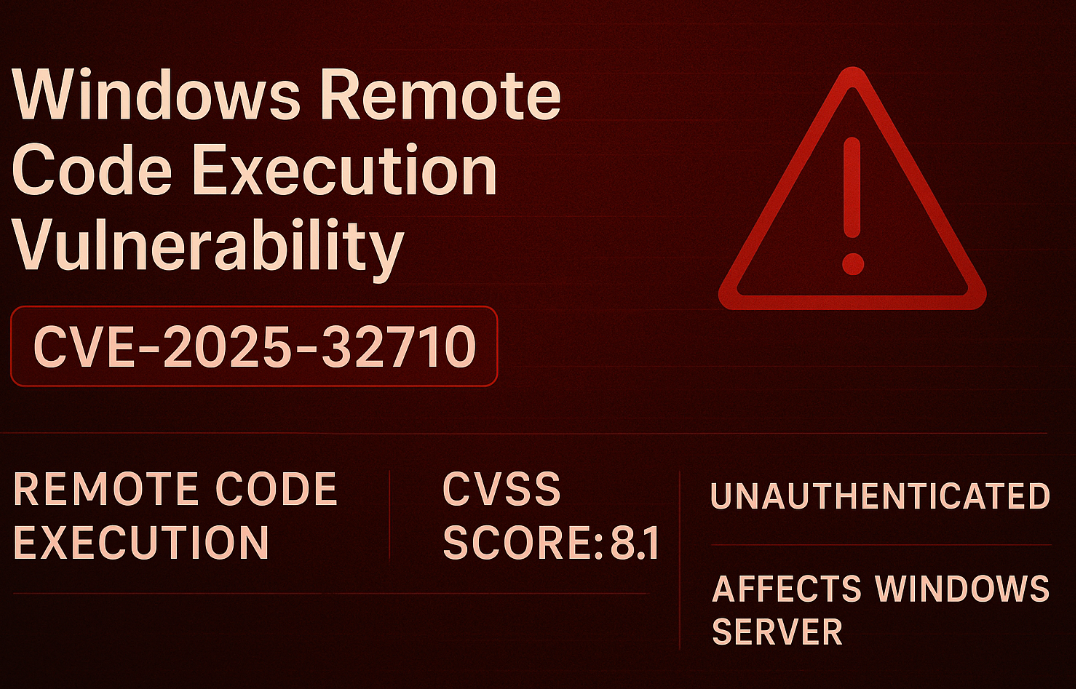
CVE-2025-32710: Critical RCE Flaw in Windows Remote Desktop Gateway
A newly disclosed critical security vulnerability in Windows Remote Desktop Services, tracked as CVE-2025-32710, enables unauthenticated remote code execution on vulnerable systems. Microsoft released the advisory on June 10, 2025, assigning the vulnerability a CVSS v3.1 score of 8.1, signaling high severity with a broad impact across multiple Windows Server platforms.
Root Cause: Memory Corruption via Race Condition
The flaw arises from a dangerous combination of a use-after-free condition and a race condition in the Remote Desktop Gateway (RD Gateway) component. By manipulating concurrent memory operations, an attacker could remotely exploit this logic flaw to execute arbitrary code with system-level privileges, all without authentication or user interaction.
This vulnerability falls under two major CWE classifications:
- CWE-416: Use After Free
- CWE-362: Concurrent Execution using Shared Resource with Improper Synchronization
The vulnerability’s CVSS vector — CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C — describes a network-accessible attack with no privilege or user interaction required, but one that demands high technical complexity, especially to win the race condition reliably.
To interpretate the CVSS vector use CyberRiskEvaluator
Technical Exploitation
Attackers connect to an RD Gateway-enabled system and manipulate memory allocation timing to induce a use-after-free scenario. If successful, they gain access to and control over freed memory areas, allowing the injection and execution of malicious code at the kernel level.
Despite the complexity, a determined adversary with sufficient resources could exploit this bug to gain full system access, elevate privileges, extract sensitive data, modify configurations, or bring down services entirely — thus impacting confidentiality, integrity, and availability (CIA) at the highest level.
Risk Factors Overview
| Attribute | Details |
|---|---|
| CVE ID | CVE-2025-32710 |
| Impact | Remote Code Execution (RCE) |
| Exploit Prerequisites | Network access to RDP Gateway; successful triggering of race condition |
| Severity | High (CVSS 8.1) |
| Discovery Credit | SmallerDragon & ʌ!ɔ⊥ojv (Kunlun Lab) |
Affected Systems and Patch Details
Microsoft has confirmed that the following Windows Server versions are vulnerable:
- Windows Server 2008 (32-bit/x64, SP2)
- Windows Server 2008 R2
- Windows Server 2012 / 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
- Windows Server 2025
Each version has corresponding Knowledge Base (KB) updates:
| Server Version | KB Update(s) | Target Build Version |
|---|---|---|
| Server 2025 | KB5058411, KB5058497 | 10.0.26100.4061 |
| Server 2022 | KB5058385, KB5058500 | 10.0.20348.3692 |
| Server 2008 | KB5061198, KB5058429 | 6.0.6003.23317 |
These updates are distributed through Windows Update, WSUS, and the Microsoft Update Catalog. Server Core installations are equally impacted and require patching.
Exploitability and Mitigation Guidance
Although categorized as “Exploitation Less Likely” due to the need to win a race condition, organizations should not underestimate the threat. No active exploitation has been observed to date, but the sophistication of malware developers and state-level actors makes this a potential high-value target.
Recommended Actions:
- Immediately apply June 2025 security updates to all affected Windows Server systems.
- Restrict RD Gateway access using network segmentation, firewalls, and VPN controls.
- Enable advanced endpoint protection, such as Microsoft Defender, with real-time protection and EDR.
- Log and monitor all RDP traffic for anomalies.
- Review and update incident response plans to include race condition and memory corruption scenarios.
Conclusion
CVE-2025-32710 is a complex yet high-impact remote execution vulnerability affecting core components of enterprise IT infrastructure. The potential for full system compromise underscores the importance of rapid patch management, network hardening, and strategic threat monitoring.
As RDP services continue to be a common attack vector for ransomware and APT groups, defenders must act decisively — patch now, and harden your perimeter.